Key Facts
- Manual, paper-based visitor logs create blind spots, expose personal data, and make it hard to prove who accessed which area and when. Modern visitor management systems (VMS) provide automated visitor logging, ID verification, signatures, and acknowledgments. This approach turns the reception desk into a controlled compliance checkpoint.
- Centralized, encrypted, transparent visitor logs support key frameworks such as GDPR, HIPAA, ISO 27001, OSHA, FDA, and other industry-specific regulations.
- Real-time dashboards, alerts, and role-based access control improve transparency and ensure that only authorized stakeholders see sensitive visitor data.
- Highly regulated environments — healthcare, logistics, government, manufacturing, pharma, and data centers — rely on VMS for audit-ready traceability and incident investigations.
In regulated industries, the simple act of letting someone walk through the door is loaded with legal and security implications. Paper sign-in sheets and manual processes can no longer keep up with today’s expectations for transparency and real-time visitor monitoring. That’s where a modern visitor management system (VMS) steps in.
Thanks to the audit-ready check-in system, visitor compliance tracking, and secure storage of access records, the reception area is turned into a controlled entry point instead of a weak link. In this article, we will explore how VMS solutions support compliance, improve visibility, and help organizations prove exactly who was on site, when, and why.
Replace paper logs with a digital visitor management system.
Why Transparency and Compliance Matter in Modern Organizations
A modern visitor management kiosk replaces the old sign-in sheets. Digital systems like this can bring structure and security to the front desk.
Rising regulatory pressure in healthcare, logistics, government, and manufacturing
Healthcare organizations, for example, face hefty penalties under laws like HIPAA if unauthorized individuals access restricted areas. In logistics, programs like the U.S. Customs-Trade Partnership Against Terrorism (C-TPAT) require detailed visitor logs at warehouses and ports.
Government buildings present a dual mandate of security and public accountability as well. Manufacturing facilities should also be compliant with the workplace safety mandates (like OSHA regulations) and quality standards.
Importance of traceability and access records
If an incident occurs, investigators and regulators will immediately ask for access records of the facility: Who was in the data center at 2 PM last Tuesday when the system went down? Which contractor entered the sterile pharma production room before a batch was contaminated?
The benefits of real-time access to records extend to emergencies as well — during a fire or evacuation, lives may be lost if you don’t know exactly who is inside the building.
Common compliance risks with manual check-in processes
Old-fashioned manual visitor logs create blind spots and liabilities. They expose private info to unintended eyes, rely on memory and penmanship for accuracy, and fail to provide real-time visibility. As a result, they leave organizations unprepared for audits or emergencies.
It’s the mundane slip-ups that may seem “innocent” at first glance — a missing signature here, a lost sign-in sheet there — that quietly erode compliance.

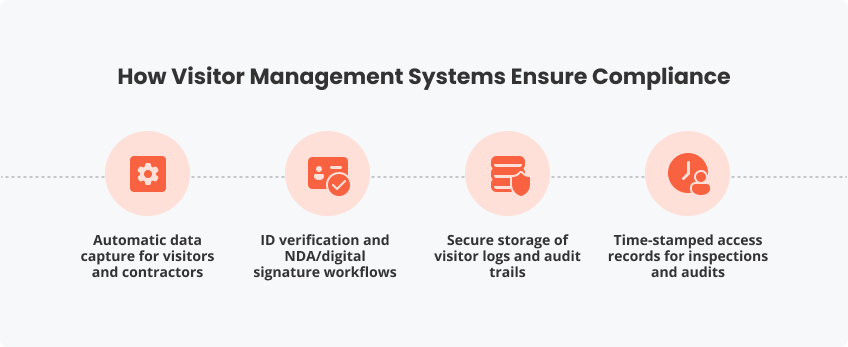
How Visitor Management Systems Ensure Compliance
A digitized, traceable check-in process does more than speed up the lobby experience — it fundamentally transforms data protection strategy. A secure visitor registration system acts as a digital gatekeeper that automatically enforces necessary compliance checkpoints.
Automatic data capture for visitors and contractors
Automatic data capture and badge issuance mean nothing would fall through the cracks. All visitors and contractors are consistently logged, identified, and managed in accordance with the established data protection policies, strengthening overall contractor compliance.
ID verification and NDA/digital signature workflows
VMS workflows verify IDs, collect signatures, and record acknowledgments without the necessity to stockpile paper. This not only saves time for both visitors and staff but also creates a defensible record. This record proves that your organization follows laws and best practices.
Secure storage of visitor logs and audit trails
A VMS doesn’t just log visitor information; it locks it down. Thanks to the protected visitor management system, you have a centralized, encrypted vault of visitor activity that is difficult to tamper with. Besides, this digital system is easy to audit.
Time-stamped access records for inspections and audits
Accurate timestamps for every visitor’s journey in your facility are immensely valuable. These access logs for inspections are immensely helpful in case of a routine safety inspection, a surprise regulatory audit, or an investigation after an incident. Thanks to the automatically provided timestamps, organizations can easily obtain a factual narrative of who and when entered the facility, creating a detailed visitor access audit trail.
Enhancing Transparency with Real-Time Visibility
Beyond just logging data for later, a good VMS enhances both security and openness with real-time visibility with the help of dashboards and digital alerts.
Live dashboards of on-site visitor data
Real-time dashboards turn visitor management from just a static record-keeping exercise into a dynamic situational awareness tool. They bring transparency to the present moment, not just the past, which is truly invaluable for security, safety, and operational efficiency of the company, especially in organizations that need multisite visitor transparency.
Role-based access control (RBAC) and permissions
RBAC lets organizations share real-time visitor information appropriately. For example, access control can help build full security oversight, provide department managers insight into their guests, and give auditors access to historical logs — while preventing unauthorized eyes from wandering through sensitive data.
Integration with access control and security systems
After the integration with physical access control, surveillance, and communication systems, a VMS becomes an integral part of the organization’s wider security ecosystem. It enhances transparency by linking visitor identity to physical movement data and boosts digital compliance management.

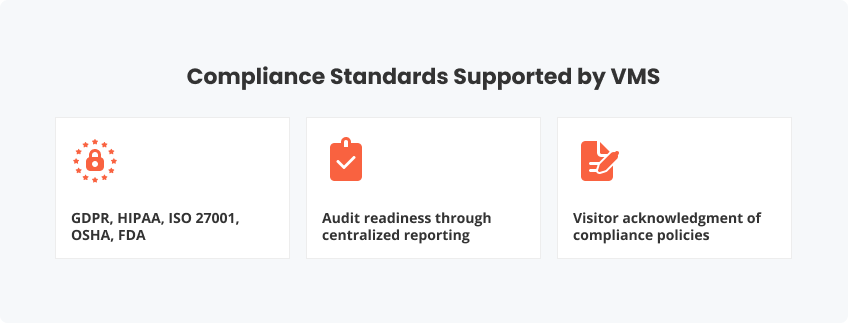
Compliance Standards Supported by VMS
Most modern VMS platforms are built with regulatory compliance and industry-specific standards in mind. Let’s highlight some major frameworks and how a VMS helps companies stay compliant with them.
GDPR, HIPAA, ISO 27001, OSHA, FDA
- Data Privacy (GDPR, CCPA, etc.): In jurisdictions like the EU, visitor information (names, contact info, photos, etc.) is considered personal data protected under laws such as the General Data Protection Regulation (GDPR). A visitor system helps comply with GDPR, secure that data, and respect privacy rights.
- Healthcare (HIPAA): In healthcare environments, HIPAA rules require that the facility safeguard Protected Health Information and establish control over access to restricted areas. For example, a VMS can limit visitor access to only certain departments and flag if an unauthorized person tries to enter the prohibited area.
- Information Security (ISO 27001): ISO/IEC 27001 is an international standard for information security management. It actually explicitly calls out physical security controls, including visitor management: Annex A.7.2 of ISO 27001:2022 has a straightforward requirement that organizations should log visitors and then safely keep those logs ready for audit.
- Workplace Safety (OSHA and equivalents): Occupational safety regulations (like OSHA in the US) mandate that employers keep workplaces safe for everyone, including all visitors and contractors. For example, to comply with these regulations, you can use a VMS that will inform visitors of the requirement to watch a safety briefing video before entering the potentially hazardous area.
- Industry-specific (FDA, ITAR, etc.): Many industries have their own rules. The FDA’s requirements for drug manufacturing don’t explicitly say “use a VMS,” but they still require control over the environment to prevent mix-ups and contamination. The knowledge of who entered a production area will be helpful in ensuring a high level of control. Meanwhile, ITAR (applicable to defense-related industries) does explicitly require keeping visitor records and verifying nationality, which is possible with the help of a visitor management system as well.

Audit readiness through centralized reporting
Thanks to centralized reporting, visitor data becomes a valuable compliance asset rather than an imposed liability. Overall, it means fewer surprises during audits, faster responses to inquiries, and the ability to verify internally that you are meeting standards. With a VMS, an organization can shift the narrative from reactive (“Let me gather those logs for you”) to proactive (“Here’s a report we routinely review to ensure compliance”).
Visitor acknowledgment of compliance policies
Visitor acknowledgment via VMS ensures no one enters blind to the rules. This helps companies stay compliant with regulations that demand such notification (like GDPR’s requirement of transparent data use or OSHA’s duty to inform of hazards). Besides, it fortifies the organization’s position by making expectations explicit and recorded.
Use Cases in Regulated Industries
Different industries have unique compliance concerns that a VMS can address. Let’s look at a few high-security settings and illustrate how they leverage visitor management for better compliance.
Logistics hubs: who accessed what and when
At logistics hubs, a VMS provides full traceability of who accessed what and when. This is a critical component of supply chain security. It aligns with regulatory programs (like C-TPAT’s visitor logging and escort requirements) and adds operational transparency that benefits both compliance and business efficiency.
Government buildings: public traceability and security
Government buildings leverage visitor management systems to provide traceability for public access. The implementation of VMS shows the public that the government is both open and responsible in how it manages visitor interactions. It provides security teams with the tools to enforce rules in real time, which is vital in an age of heightened security threats.
Pharmaceutical plants: batch-level visitor traceability
Pharmaceutical plants use VMS to achieve a fine-grained level of visitor traceability and control that manual methods cannot provide. They link people to specific areas and batches, which bolsters compliance with GMP principles of preventing contamination and keeping thorough records.
Data centers: full audit logs and time-limited access
For data centers, a visitor management system provides full-spectrum visibility and control over physical access. It logs every entry/exit in detail, limits access in duration and scope, and provides the evidence needed for a wide range of audits. By eliminating anonymity, it creates a culture of accountability that clients of the data center also appreciate.
Choose visitor kiosks that fit your brand and compliance needs.
Implementation Best Practices
Choosing and configuring a visitor management system is only the beginning of the journey. To truly harness its benefits, organizations should follow best practices during implementation.
Custom compliance fields and legal documents
To collect every bit of information and every agreement your compliance landscape demands, tailor your VMS appropriately. It’s much easier to do it upfront in the visitor workflow than to chase it later.
Multilingual support for global compliance
If you operate in a multilingual environment, don’t treat language support as an afterthought. You should bake it into your VMS configuration from day one. It will lead to more accurate data capture and a smoother visitor experience, reflecting well on your organization’s professionalism.
Cloud-based vs. on-premises compliance strategies
Align your VMS deployment model with your compliance needs and risk appetite. Cloud is often advantageous for most, provided the vendor aligns with your data protection requirements. On-premises might be necessary for highly sensitive contexts. Whichever you choose, document the reasons — it shows auditors that you deliberately selected the model that best protects your visitor data.
FAQ
Absolutely! A VMS can bolster your legal audit readiness. It essentially acts as an automated record-keeper that can be trusted to provide accurate records of facility access, which is a common area of scrutiny in audits and legal proceedings.
The storage duration for visitor logs is usually configurable and often guided by legal requirements or company policy. It’s up to you to decide how long to store visitor logs based on legal needs and your preferences.
It can be, absolutely — if implemented correctly. If you configure it with appropriate privacy notices, consents, security controls, and data management practices, VMS data will stay compliant with GDPR, HIPAA, and similar frameworks.
Any place with a front door, really — but the biggest beneficiaries are industries with strict compliance requirements or high security needs. These are places where a lapse in knowing who’s on-site can lead to compliance fines, security breaches, or safety incidents.